Cryptographic Circuits with Logic Level Countermeasures against DPA
The hardware security team at Matsumoto Laboratory, Yokohama National University, studies the side-channel security of cryptographic circuits implemented on security chips as a part of the research on the methodology for the Logic Level countermeasures against DPA --- Differential Power Analysis. In order to accurately evaluate the vulnerabilities and performances of the circuits with countermeasures, we developed four AES circuits to which different existing countermeasures are applied. The developed IP cores (Verilog-HDL source files) and the pointers to the corresponding countermeasures are listed below. These IP cores were customized for the project Standard Cryptographic LSIs conducted by AIST and sponsored by METI. The resultant IP cores were actually mounted on two cryptographic LSIs fabricated with 90-nm and 130-nm TSMC standard cell libraries. A platform called SASEBO-R has been developed to evaluate the cryptographic LSIs by the same project.YNU_MA_AESTOP
An AES encryption circuit (128-bit key only) with DPA countermeasure MAO (Masked AND Operation) proposed by paper [1].
[1] E. Trichina, ``Combinational Logic Design for AES SubByte Transformation on Masked Data," Cryptology ePrint Archive, 2003/236, 2003.
YNU_WL_AESTOP
An AES encryption circuit (128-bit key only) with DPA countermeasure WDDL (Wave Dynamic Differential Logic) proposed by paper [2].
[2] K. Tiri and I. Verbauwhede, ``A Logic Level Design Methodology for a Secure DPA Resistant ASIC or FPGA Implementation," DATE 2004, pp.246-251, 2004.
YNU_ML_AESTOP
An AES encryption circuit (128-bit key only) with DPA countermeasure MDPL (Masked Dual-Rail Pre-charge Logic) proposed by paper [3].
[3] T. Popp and S. Mangard, ``Masked Dual-Rail Pre-charge Logic: DPA-Resistance Without Routing Constraints," CHES 2005, LNCS 3659, pp.172--186, Springer, 2005.
YNU_TI_AESTOP
An AES encryption circuit (128-bit key only) with DPA countermeasure TI (Threshold Implementation) proposed by paper [4].
[4] S. Nikova, C. Rechberger and V. Rijmen `` Threshold Implementations Against Side-Channel Attacks and Glitches," ICICS 2006, LNCS 4307, pp.529-545, Springer, 2006.
Table I shows the performances of all the IP cores on all the target devices. The experimental cryptographic LSIs (ASICs and FPGA) that contain these AES co-processors are supposed to be operated at a low frequency of 24 MHz, and so speed constraints for the circuits are not specifically given to the logic synthesis tool.
| Evaluation item | No countermeasure | MAO(MA) | WDDL(WL) | MDPL(ML) | TI |
| 130nm-ASIC | |||||
| Gate counts [Kgate] | 13.5 | 34.1 | 29.4 | 118.6 | 107.1 |
| Maximum operating frequency [MHz] | 68.9 | 49.4 | 46.1 | 20.2 | 48.3 |
| Processing performance [Mbps] | 802 | 575 | 281 | 123 | 562 |
| 90nm-ASIC | |||||
| Gate counts [Kgate] | 12.2 | 29.4 | 29.3 | 106.1 | 93.9 |
| Maximum operating frequency [MHz] | 83.9 | 60.5 | 67.8 | 25.1 | 63.7 |
| Processing performance [Mbps] | 977 | 704 | 413 | 153 | 742 |
| FPGA (Xilinx Virtex2Pro XC2VP30-4) | |||||
| No. of SLICE | 1,445 | 3,017 | 2,744 | 12,691 | 10,619 |
| Maximum operating frequency [MHz] | 55.7 | 44.0 | 25.4 | 15.7 | 63.7 |
| Processing performance [Mbps] | 648 | 512 | 155 | 96 | 337 |
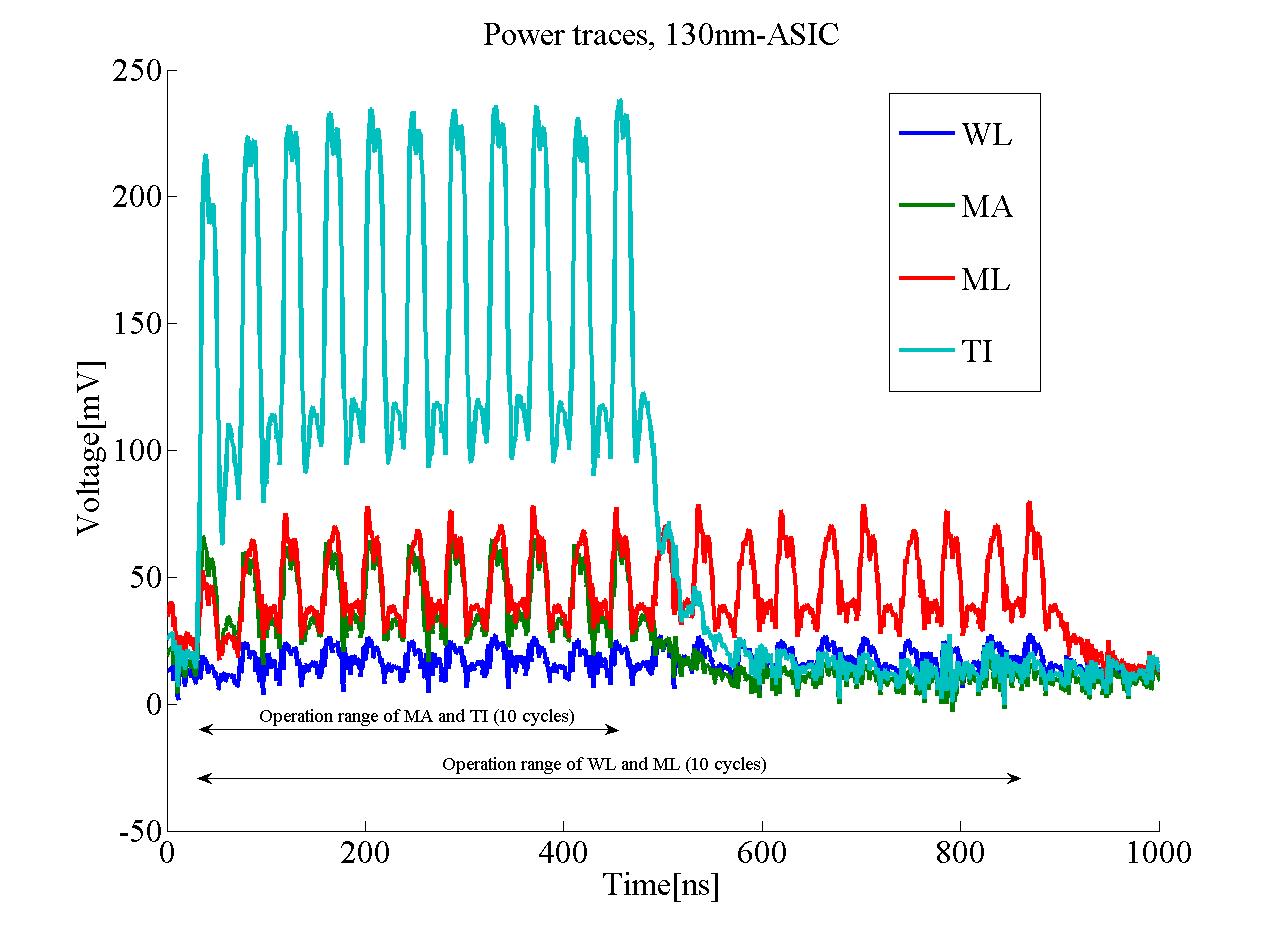
The figure below shows the average power traces of all the IP cores on 130-nm ASIC. You can obtain such a trace by yourself if you access each AES co-processor by a proper procedure using SASEBO-R.
Revision History:
2010.02.05 Released.
2010.03.31 Revised.
Copyright(c) 2010, YNU MLAB TRH Team